An Interest In:
Web News this Week
- April 2, 2024
- April 1, 2024
- March 31, 2024
- March 30, 2024
- March 29, 2024
- March 28, 2024
- March 27, 2024
Developers Guide to DevSecOps
DevOps helps businesses speed up software development and deployment cycles while automating processes, monitoring performance, and improving security. The DevSecOps movement takes all of the benefits of DevOps and adds on security practices and methods so businesses can build secure software faster.
A company's security team is responsible for carrying out a risk assessment and penetration testing. It is also their responsibility to identify the vulnerabilities, threats and risks that may lead to a breach. The team then implements countermeasures to protect the organization from potential cyber-attacks. Security testing is an important part of the security process in any organization. It helps identify weak spots and vulnerabilities in the system before they are exploited by hackers, thereby reducing the chances of data breaches.
Its important to know that the goal of testing is not just to find security vulnerabilities. Instead, its to assess the risk associated with a given vulnerability or set of vulnerabilities. The test aims to determine whether an application has flaws that attackers can exploit and, if so, what those flaws are. This blog post will cover every important aspect you need to know about security testing and DevSecOps.
What is DevSecOps?
In todays modern business environment, every company is a software company. Therefore, companies should optimize their software development lifecycle to ensure they get the most out of their software engineering investments. This means that businesses should adopt DevOps and modern cloud-native methodologies to improve efficiency and effectiveness in their software engineering processes. Even though companies have DevOps teams, security is somehow getting left behind or, most often, ignored. Sometimes, its left up to the security teams alone.
Where DevOps brings together development organizations and operations teams, the DevSecOps culture (or, development security and operations) adds in the objectives of security teams for shared responsibility. Almost every organization today has some form of technology integral to their operations. Infrastructure security is imperative, and simply adding in security measures for employees is not enough. DevSecOps takes security to the next level with secure code, release management, automated security checks, security controls, and more all in the production environment before code reaches users. In short, DevSecOps bridges the divide between development, operations, and security practitioners.
This all means many companies are not taking the necessary steps to ensure their software systems, methods, and applications are secure. This has led to a new term in the industry DevSecOps.
The DevSecOps methodology was created by Netflix, Etsy, and Amazon Web Services as they faced an onslaught of cyberattacks that threatened their business continuity. DevSecOps implementation helped these companies improve their response time by moving away from reactive IT practices toward proactive application development. This methodology aims to also reduce the time it takes for developers to push code into production. A DevSecOps environment can be created in any company, regardless of size or industry.
DevSecOps in the Software Development Lifecycle
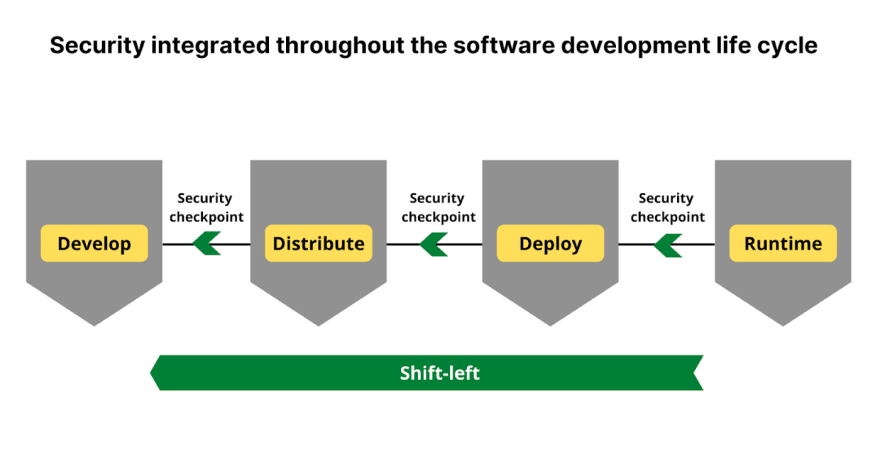
DevSecOps is a new way of approaching application security and taking it seriously rather than as an afterthought. It is an approach to securing the software development process and applications by integrating security into the software development lifecycle (SDLC). With the emergence of DevSecOps, there has been a shift in how we think about security and react to threats. While it focuses on shifting left in the SDLC, it also ensures that security is everyones job.
You could test the code changes for security vulnerabilities through a CI system even before any artifact is created, and then you could test again in between each stage to make sure the true artifcats are being passed to the next stage. DevSecOps aims to prevent security threats before they occur by implementing best security practices throughout the SDLC with more secure code.
Benefits of DevSecOps
Organizations can expect to see significant benefits from implementing a DevSecOps process. Some of the most common benefits include:
- Increased software quality and build security as developers become more serious about threats and aware of the code they contribute in software releases
- Finding the security loopholes in the applications and actions to fix them. A continuous integration (CI) tool integrated with an application security testing tool gives more visibility to the vulnerabilities in the code.
- Automation of testing processes to ensure they are kept up to date and resolve all issues quickly
- Improvement if customer experience and developer productivity
- Organizations can build software that is secure from the start by shifting left approach. This means customers will not have to worry about data breaches and can fully trust the software they are using thanks to more secure software.
- Reduced time to marke. With a DevSecOps strategy, organizations can eliminate bottlenecks resulting in deployment delays. This means companies can deliver software on time and ready to deploy.
- Increased team collaboration. A DevOps implementation encourages collaboration between the development and operations teams. A DevSecOps strategy takes this step further by including other teams, such as security and business stakeholders, in the process.
Notable DevSecOps Strategies
DevSecOps helps to address these concerns by integrating security into the development process. It also helps to secure the development environment, which is an important step in protecting against cyber attacks. We have some DevSecOps strategies listed below to tackle and mitigate security issues.
1. Automated Testing for Security Vulnerabilities
One of the biggest challenges when implementing DevSecOps is integrating a security test phase into the SDLC. For years, code testing has been something that was left behind until the end of the project. It used to be ignored, or, even if automated, it was often done poorly.
With DevSecOps, testing needs to be integrated and automated into the SDLC. Code scanners can help with identifying vulnerabilities but lack accuracy, and manual penetration testing is time-consuming and costly. Automated tools can be used to detect vulnerabilities and enforce security standards along with policies. In addition, security tools can be used to identify vulnerabilities in code.
2. Some DevSecOps tools and practices include:
- Code-level testing is done by inspecting the code and looking for dangerous packages, insecure configurations, and risky parameters.
- Code scanners can help find unsafe functions like strcpy or unsecured calls to system commands
- Configuration management prevents issues that could allow unauthorized users to access sensitive data.
- Through dynamic application security testing (DAST), potentially risky parameters are being passed to a function, which could be manipulated to cause malicious actions.
Harness Security Testing Orchestration (STO) is one such tool that can help organizations prioritize application security vulnerability data and deliver highly secure applications while maintaining deployment velocity and minimizing rework. 
3. DevSecOps and Continuous Integration and Continuous Delivery (CI/CD)
Another significant concept in DevSecOps is employing CI/CD. CI/CD helps development teams automate code commits, build and test the code, and deploy it to the specified environment. In addition, developers can automate testing to find security issues in their application code by integrating application security as part of their production environment pipeline. Therefore, having a robust CI/CD platform is a must and the prerequisite to do DevSecOps because it integreatse continuous monitoring into development cycles. At different stages of the DevOps pipeline, we can have security checkpoints such as vulnerability scanning, JIRA approvals, adherence to governance and security policy, software composition analysis, and more.
4. Development Teams Test Hard and Test Smart
Your development team needs to act like hackers and security breachers and do not give any chance for them to enter your SDLC premises. By configuring your development cycle with all the possible security analysis and testing tools. With platforms like Harness, integration with any test suite is possible. Make sure you configure from simple tests to load tests to availability tests, so your CI/CD pipeline is attack free. 
You can see that the above CI/CD pipeline is configured with various testing suites, which ensures security for the application.
5. Culture of Automation and Ownership
Another vital aspect of DevSecOps is the culture of automation and ownership. Developers need to be given the freedom to automate processes independently, but they also need to own their code. This means they are responsible for everything in their code, including the security risks. Developers also need to be given the tools to automate processes efficiently. For example, if you want to automate testing, you must have procedures and tools to run these tests. Many tools can help with automation, such as OWASP ZAP, Burp Suite, or Twist. These tools can be integrated into the code delivery process and trigger automated security tests at different stages.
6. Determine Risk Based on the Criticality of Assets

Another critical aspect of DevSecOps is determining the risk based on the criticality of assets. You cant treat every change the same; some might pose big risks, while others dont. When it comes to security, you need to know what risks are in your application. This can be done by using a risk-based approach. You can use a risk-impact matrix to identify risks and assign them a severity based on how they affect your application. You can also use a risk-grade model that helps you identify risks and set a priority for them. This can all be done using platforms like Harness's STO (Security Testing Orchestration).
The Harness STO has the capability to centralize security logs and results from over 40+ security scanners into a single dashboard of results. Data centralization also allows you to kick off continuous improvement initiatives. When data is in silos, it is much harder to analyze the results of the development, and hence the quality of improvements will be low.
7. Have Secrets Management in Place
Your applications will have some type of valuable credentials. It is very critical to ensure the encryption of such credentials and valuable information through secrets management. It can be your GitHub repo auth secrets, database credentials, etc. If such things are leaked, the attackers can easily exploit and pose a security threat. With platforms like Harness, it becomes very easy to keep our application secrets as they get encrypted through Harness secret manager. 
8. Establish a Security Review Process for Code Changes
Once you know what risks are in your application, its important to establish a security review process for code changes. This will help you to track changes and identify which team member is responsible for each change. It can also help you identify patterns in the code and see if any vulnerabilities have been introduced or have not been resolved since the last code review.
9. Monitor for Threats and Anomalies in Real-Time
The threats and anomalies can be monitored in real time with the help of threat intelligence and anomaly detection. Threat intelligence is the process of gathering, analyzing, and distributing cyber threat information in real-time. It includes malware alerts, network signatures, and malicious IP addresses. Threat intelligence can help identify observed threats and has been proven to work in real time. Its essential to monitor for threats and anomalies in real time because threats are evolving and must be resolved as soon as possible.
The Need for DevSecOps
Businesses must implement DevSecOps, as it will help them to keep their software and applications secure while increasing their speed to market. Adopting DevSecOps has numerous benefits, as we mentioned above in the article. Tackling security issues to patch common vulnerabilities is now possible with DevSecOps practices. Everything from writing code and testing to deploying applications needs to be approached from a new angle when adopting DevSecOps principles. With platforms like Harness, it becomes a reality to handle these complex vulnerabilities, integrate security in the SDLC and streamline the software delivery.
Original Link: https://dev.to/pavanbelagatti/a-developers-guide-to-devsecops-33nl
Dev To
 An online community for sharing and discovering great ideas, having debates, and making friends
An online community for sharing and discovering great ideas, having debates, and making friendsMore About this Source Visit Dev To