An Interest In:
Web News this Week
- April 18, 2024
- April 17, 2024
- April 16, 2024
- April 15, 2024
- April 14, 2024
- April 13, 2024
- April 12, 2024
All You Need to Know FIDO2 & Passwordless Authentication
In this Blog, I'm gonna tell you all about Passwords, current authentication models, and what is wrong with them, along with RSA encryption, trusted computing, and finally FIDO2.
Authentication models and Passwords
Fun fact: The concept of Password was invented by Fernando Corbat in 1960 at MIT. It was first used on an IBM Mainframe to keep individual files private to a user. It paved the way for Personal Identification Numbers (PIN) based authentication in the 1980s.
I hope you agree with me that Passwords are very Vulnerable to Brute force, Password Guessing, and Phishing attacks. According to SplashData, the top two passwords used from 2011 to 2018 were password and 123456.
Current authentication models use one (single-factor) or multiple (multi-factor authentication) of the following:
- Something the user knows. (PIN, Passwords.)
- Something the user has. (ATM card, Phones, security keys)
- Something the user is. (Biometrics)
- Something the user produces. (Speech recognition, Signature)
It is to be noted that most of them have one or the other vulnerability.
This diagram shows how authentications are done. It is pretty self-explanatory
Drawbacks of authentication models:
- Something the user knows: Can be extracted by social engineering like phishing.
- Something the user has: OTPs fall into something the user knows before it is typed. ATM cards can be skimmed.
- Something the user is: Biometrics can be cloned. For example, fingerprints can be regenerated by even high-resolution pictures. Deepfakes can be used to trick facial recognition.
- Something the user produces: Vulnerable to replay attacks.
Things are never 100% secure, so focus on adequate security.
Focus on the scalable attacks first.
Passwordless Authentication:
Here comes the hero of the story: Passwordless Authentication. It generally comes down to the authentication model of Something the user has and/or Something the user is
A few examples are push-notification login and security keys.
- In push notification login, no matter what device you are logging in from, you will get a notification on your smartphone which you have to approve.
- In security keys, you need to carry a device like a smart card which you need to connect to the machine you are logging in from for logging in.
Now if you are like me you must be thinking how does it work? For that, we need to understand a few concepts like RSA and Trusted Computing.
Basic concepts of RSA
Public Key Cryptosystem (PKC): There are two keys (known as a key pair): Public key and Private key. If one key is used to encrypt a piece of data, the other can be used to decrypt it.
Losing the private key compromises the key pair. The public key can be shared easily.
Works on the principle that computers cannot efficiently prime factorize a number. (Unless using Shors algorithm but we are not going into quantum computing now so keeping that aside.)
RSA Cryptosystem has been proven to be a strong cryptosystem. Now it is up to us keep the keys secure and use them well.
There are 3 steps basically:
1. Key pair generation:
Choose two very large prime numbers p and q. Each over 1024 bits and a multiple of 256 bits in size.
n=p*q
(n)=(p-1)*(q-1) (It is to be noted that n cannot be prime factorized easily, so n cannot be deduced from (n))
Select a number e where 1<e<(n), e co-prime to (n).
Calculate d such that d=e-1 mod (n)
Announce public key kpub={ n, e}
Keep private key secret kpr={ n, d}
2. Encryption for authentication:
If we have a plaintext number P and Kpr= { n, d},
C=P^d mod N
Here C is the cipher text.
(For the exponentiation, we use Fast Exponentiation algorithm)
3. Decryption for authentication:
If we have a ciphertext number C and Kpub= { n, e},
P=C^e mod N
Here P is the plain text.
(For the exponentiation, we use Fast Exponentiation algorithm)
To understand RSA better check out the resources section of the blog.
Trusted Computing
Trusted Platforms are devices embedded on the motherboard or in the CPU. It is used for cryptographic applications. When used for RSA, the private keys never leave the hardware, making it secure.
Some popular ones are Samsung Knox, Apple Secure Enclave, Google Titan, Windows Hello etc.
Physical Security Key on the other hand is like a Trusted Computing Platform but lightweight and portable. It needs to be connected to the device while logging in. Some smartwatches can also be used as security keys. Can be usually connected via USB, BLE, or NFC.
FIDO2
FIDO2 is the best option for passage identification. To understand it better lets go through some of its components:
- Client browser: The web browser we are using
- Authenticator attachment: Physical security key or internal trusted computing module. It is of two types: Platform: Internal authenticator, Cross-platform: External security key
- Relying Party (RP) Server: The website we are logging in to.
- RP ID: The URL of the RP Server.
- Challenge: A small text which can be encrypted and decrypted to check whether the keypair is valid.
Specifications used in FIDO2:
- W3C WebAuthn: It is the set of protocols that define how the server interact with the web browser.
- Client To Authenticator Protocol (CTAP): It is the set of protocols that define how the web browser interact with the authenticator attachment.
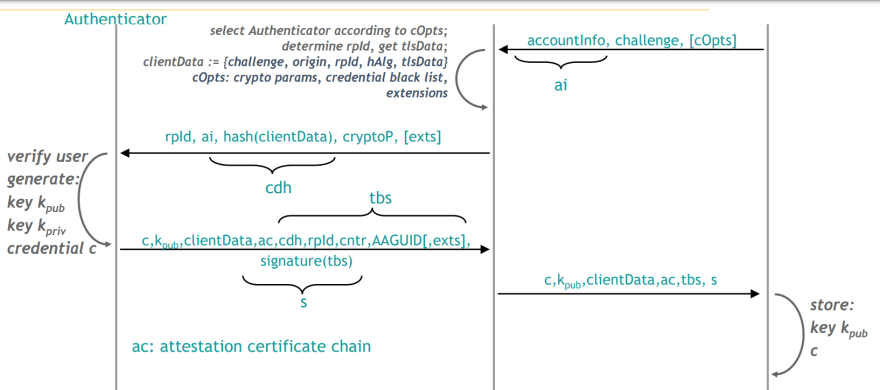
Before a key can used for passwordless authentication, it needs to be registered on the fido server.
Authentication with FIDO2 follows a similar procedure
What makes FIDO2 strong?
- Use of public key cryptosystem.
- Use of trusted computing where the private keys never leave the users device/security key.
- RP ID is verified at every step to stop Man In The Middle (MITM) attacks.
- Cannot be phished as the client is verified by RP.
- User does not have to know any information to be able to log in.
- Follows zero-trust model.
Resources to work on FIDO2
https://fidoalliance.org
https://loginwithfido.com
https://w3.org/TR/webauthn-2/
https://fidoalliance.org/specs/fido-v2.1-ps-20210615/fido-client-to-authenticator-protocol-v2.1-ps-20210615.html
https://github.com/yubico/Python-Fido2
https://github.com/yubico/libfido2
HOPEFULLY, YOU CAN WORK USING FIDO2 NOW
Original Link: https://dev.to/rishitashaw/all-you-need-to-know-fido2-passwordless-authentication-329a
Dev To
 An online community for sharing and discovering great ideas, having debates, and making friends
An online community for sharing and discovering great ideas, having debates, and making friendsMore About this Source Visit Dev To