An Interest In:
Web News this Week
- April 24, 2024
- April 23, 2024
- April 22, 2024
- April 21, 2024
- April 20, 2024
- April 19, 2024
- April 18, 2024
Detect vulnerable libraries within your GitHub environments for free
Combine the power of GitHub Actions for automated Continuous Integration/Continuous Deployment (CI/CD) pipelines with Contrast Securitys powerful free developer tool, CodeSec, to identify vulnerable dependencies in your Java, .NET, NodeJS, Ruby, Python, Go or PHP projects.
The first step is to install CodeSec locally. CodeSec is at the free tier of Contrast Securitys product suite. It is very easy to install with either Homebrew, npm or straight from binary. You can find CodeSec at Contrasts Developer Central online portal.
Once CodeSec is installed on your machine, you will need to run the command contrast config. This will give you the CodeSec account keys that you can use in your projects GitHub Actions configuration file.
CodeSec config keys
Second, you need to set those keys as secrets in your GitHub repositorys settings. This is available in your GitHub project repository on the Settings tab, Security section, Secrets option, Actions sub-option. Add secrets with the names CONTRAST_API_KEY, CONTRAST_ORGANIZATION_ID and CONTRAST_AUTH_HEADER along with their corresponding values from the contrast config command.
Add GitHub repository secrets
With those config keys set as repository secrets, you are now ready to use the Contrast SCA GitHub Action. Contrast SCA is an enterprise-level cybersecurity tool that identifies vulnerabilities in the third-party components that your project uses.
The Contrast SCA GitHub Action page gives examples of GitHub Action configuration files for use with several different languages. In this article we will walk through an example of using the NodeJS config file.
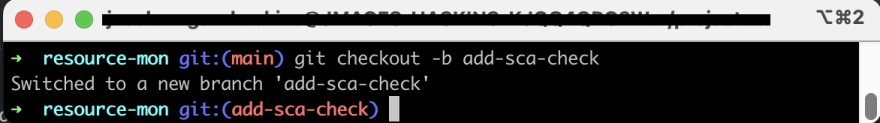
Create a new Git branch in your project with git checkout -b your-branch-name.
Create a new Git branch
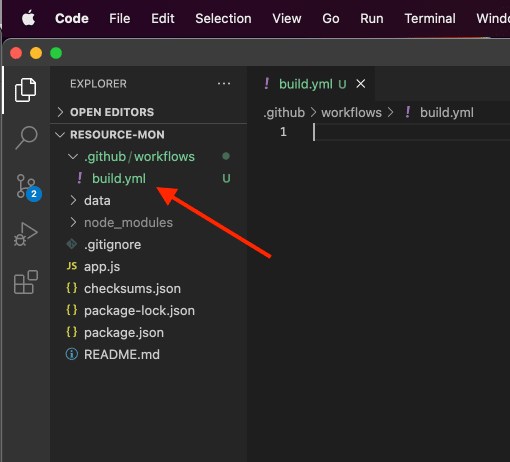
Next, create a new GitHub Actions build file at ./.github/workflows/build.yml, if your project does not have one yet. If it does, you may want to just edit your existing file.
New GitHub Actions build configuration file
Then, in the build.yml file, add the job to run the Contrast SCA action. Use the Node template from the Contrast SCA GitHub Action page. Be sure that it uses the CodeSec config secrets that you made at the beginning of the article! Note: One difference from the template is that we wont specify the apiUrl setting and will let Contrast SCA default to the free Community Edition of the Contrast tool suite server. You will also need to customize the path to your projects config files and make sure that you target branch main, which is the default name of the repositorys primary branch on GitHub.
Example build.yml for a NodeJS project
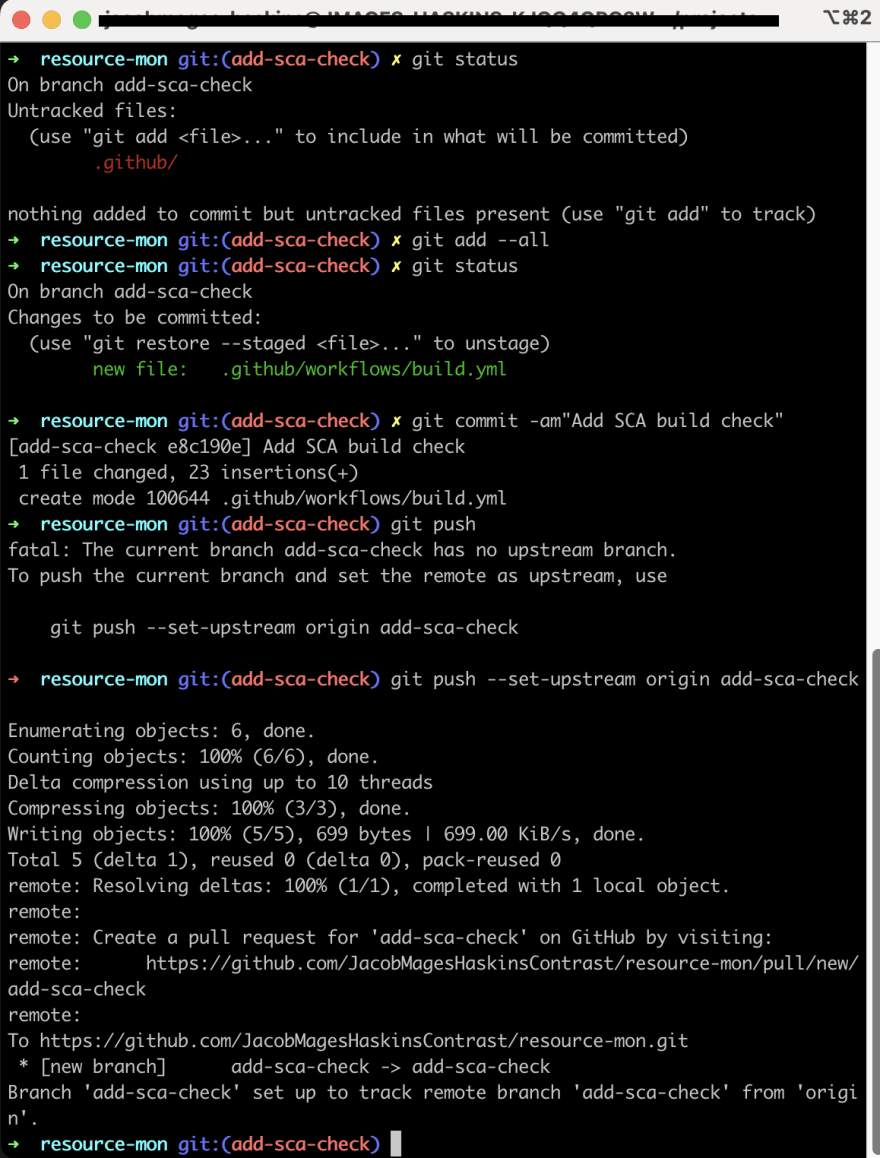
Back on the command line, add the new file to your local Git repository, commit the changes and then push it up to your remote GitHub repository.
Git add, commit and push your new build file
The output of git push gives you a URL to use to create the pull request for your changes. In this example, it was https://github.com/JacobMagesHaskinsContrast/resource-mon/pull/new/add-sca-check.
Pull request on the GitHub repository
After merging the changes, you can look at the Actions tab and see that SCA Node is now an available workflow that runs in your repository.
SCA Node workflow in the repository actions
If your project has a vulnerability, like the deliberate example vulnerability in this project, you can click on the workflows run to see its details. In the details, you can find the specific vulnerabilities in libraries that your project uses, along with advice on fixing them.
Contrast SCA GitHub Action results
Conclusion
GitHub Actions are a powerful tool. Much could be written on all the various options available for using them to power your projects CI/CD pipelines. The Contrast SCA GitHub Action, when paired with CodeSec, is a strong new tool for securing your project from cybersecurity threats.
Test out Contrast SCAs newest GitHub Action feature for yourself with CodeSec!
To learn more about Contrast's new GitHub Action:
Click here for our video tutorial.
Click here to check us out on GitHub Marketplace.
Original Link: https://dev.to/codesec/detect-vulnerable-libraries-within-your-github-environments-for-free-2mg0
Dev To
 An online community for sharing and discovering great ideas, having debates, and making friends
An online community for sharing and discovering great ideas, having debates, and making friendsMore About this Source Visit Dev To