An Interest In:
Web News this Week
- April 20, 2024
- April 19, 2024
- April 18, 2024
- April 17, 2024
- April 16, 2024
- April 15, 2024
- April 14, 2024
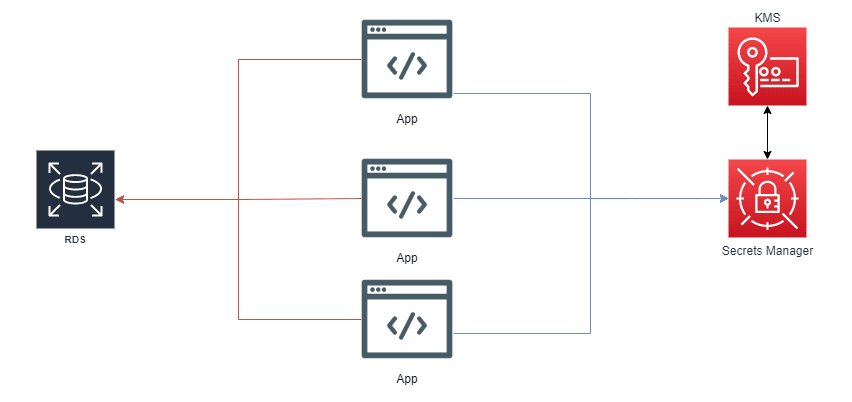
Keeping Your Data Safe with AWS Secrets Manager
Whenever we think of software that needs some sort of key management, we must challenge ourselves to seek more and more security and improve the way we manage and obtain our keys/passwords. Keeping passwords secure is not always a developer's priority during the software development process.
For this task, for example, we can use secrets management tools (methods for managing digital authentication credentials (secrets), such as passwords, keys, APIs, and tokens. One example is HashiCorp Vault, a secret management tool specifically designed to control access to sensitive credentials in a low-trust environment. It's simple to use, but you need to manage a server to run it as a service. If you have a team to do this, awesome. But if you don't, it's a risk we might not want to take... Your entire application, which depends on it, could crash.
The good news is that with the release of AWS Secrets Manager, this scenario has changed. To move forward, I assume you have some knowledge of AWS and the CLI it offers. If you haven't, I suggest taking a look here first.
P.s: when we say secrets, we mean any type of credential that is sensitive, such as bank passwords, authentication tokens, encryption passwords, etc.
AWS Secrets Manager
In April 2018, AWS released the Secrets Manager service to manage and audit secrets. It's a simple AWS service with a monthly fee of $0.40 per secret, with an additional $0.05 per 10,000 API calls. It's one of the cheapest service to maintain and manage passwords, not to mention the benefit of keeping your passwords safe almost for free.
Creating a secret
Moving forward in the AWS Management Console, select the Secrets Manager service to create a new secret.
Once inside the Secrets Manager service panel, select store new secret and then the Other types of secrets box and configure a new secret as shown below.
If you want to do it through the AWS CLI, we can get the same result with the following command.
$ aws secretsmanager create-secret --name mysupersecret --description "what secret?" --secret-string file://my_credentials.json
Inside my_credentials.json file, we have a JSON object with the fields that represent my credentials. Following our example, our my_credentials.json should have the following content:
{"apikey":"my amazing secret"}
As you can see, we can add as many lines as we need and create three types of secrets. But for our purpose, we select Other types of secrets and move forward by clicking the Next button. By clicking on next, we only define the name of our secret, which will be used later to recover it within our account. Let's name our secret mysupersecret. Finally, we will retrieve our secret programmatically. The example below is found in Golang.
package mainimport ( "github.com/aws/aws-sdk-go/aws/session" "github.com/aws/aws-sdk-go/service/secretsmanager" "fmt")func main() { sn := "mysupersecret" s := session.Must(session.NewSession()) sm := secretsmanager.New(s)output, err := sm.GetSecretValue(&secretsmanager.GetSecretValueInput{SecretId: &sn}) if err != nil { panic(err.Error()) }fmt.Println(*output.SecretString)}This is a super simple way to get our secret and use it, this way you need to configure your AWS credentials before running the code example above.
Auditing your secrets
One of Secrets Manager's features is the auditing of your quoted secrets by AWS:
() AWS Secrets Manager lets you audit and monitor secrets through integration with AWS logging, monitoring, and notification services. For example, after enabling AWS CloudTrail in an AWS Region, you can audit when a secret is stored or switched by viewing AWS CloudTrail logs. Similarly, you can configure Amazon CloudWatch to receive email messages using Amazon Simple Notification Service secrets that are not used for a period. Or configure Amazon CloudWatch Events to receive push notifications when Secrets Manager switches secrets.
Conclusion
It's an amazing service to solve real security problems of our daily life, as you can see. It is simple, easy to use and low cost.
As a company and as Vaultrarians, we love making cybersecurity easy, scalable and part of everyone's lives. How? By fully encrypting data client-side and allowing for real-time scalable data processing and computations. Also, Vaultree integrates several off-the-shelf cryptographic key management and distribution solutions including HashiCorp Vault, as well as YubiKey. We fully support a post-quantum key generation and distribution solution via Qrypt.
Wanna learn more about how our solutions work? See it yourself.
- JOIN OUR COMMUNITY ON DISCORD
For more valuable information and trends to help you keep your data safe, join our community
Original Link: https://dev.to/vaultree/keeping-your-data-safe-with-aws-secrets-manager-283c
Dev To
 An online community for sharing and discovering great ideas, having debates, and making friends
An online community for sharing and discovering great ideas, having debates, and making friendsMore About this Source Visit Dev To