Bug Bounty: Not always an ideal
I want to share with you my bug bounty experience this week and the points to remember.
(Hahaha I Know that ... my picure has nothing to do here )
So what's happen to me this week?
I joined a public bug bounty program on Intigriti, read the rules of engagement quickly, and start hacking.
Did the recon then try to find some interesting vulnerabilities.
In the target website I remarked a chat between the freelancers and the client.
I tried to submit some payload but the client side URL encode my payload, so I intercept my request with Burp and insert my payload.
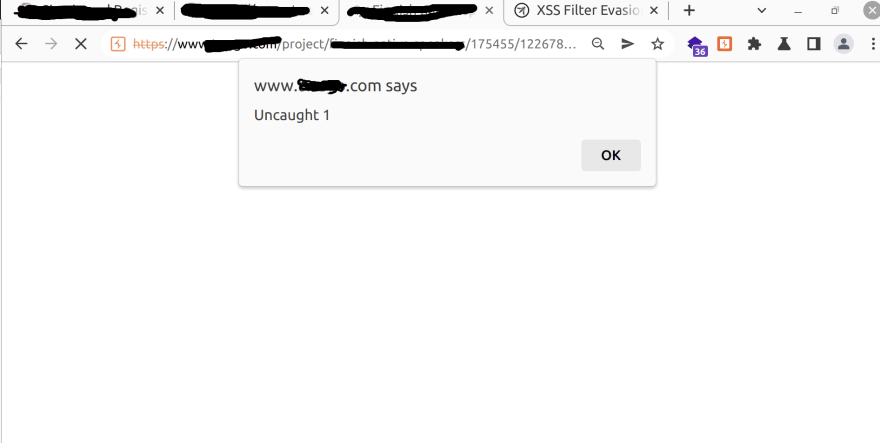
Finally at the first time I trigger a XSS with this payload:<script>onerror=alert;throw 1</script>
(with no bracket).
Before I submited my xss, I read again the rules of engagement and guess WHAT??
I can not imagine that XSS can be out of scope, even an stored XSS. So I texted intgriti team to discuss about the Stored XSS and told them to take into consideration that the severity of the XSS is HIGH, after few days a member of Intigriti team respond that: "All forms of XSS are considered as OOS for this program".
In conclusion few things that I need to learn from the next time:
Take time and read carefully the program's rules.
Chose an Bug bounty adapted to my skills.
Hope you will not fall into this trap.
Original Link: https://dev.to/nathan20/bug-bounty-not-always-an-ideal-980
Dev To
 An online community for sharing and discovering great ideas, having debates, and making friends
An online community for sharing and discovering great ideas, having debates, and making friendsMore About this Source Visit Dev To