An Interest In:
Web News this Week
- April 23, 2024
- April 22, 2024
- April 21, 2024
- April 20, 2024
- April 19, 2024
- April 18, 2024
- April 17, 2024
Encryption & decryption for r0@drunner$
The modern internet today is programmed in such a way that, the traffic is encrypted. Now, what does this encryption mean? In simple terms, encryption ensures only those who are meant to understand the information do so, and for others, it is just gibberish.
Encryption
Encryption transforms readable plaintext into unreadable ciphertext that only the intended users can understand. This prevents attackers from making sense of the data even if they get access to it. The intended users will be aware of how to convert the ciphertext into plaintext, a process known as decryption.
A simple encryption example is, say alphabet A -> 1, B -> 2, C -> 3, so on.. So the word CAB would be 321. The receiver will convert the 321 back to plain text by mapping the numbers to alphabets -> CAB.
Even though the above encryption-decryption looks simple, the modern encryption-decryption algorithms are far more complex in practice and are computationally intensive. Most encryption algorithms use a key, which could be a combination of text, numbers & special characters. This key would be used in the encryption or decryption processes. The point of using a key here is, even if the middleman knows the algorithm involved in the encryption process, they will not be able to decrypt it unless they know the key. This is like having the access to the lock, but not having the key to unlock it.
Types of Encryption Algorithms
- Symmetric algorithms
- Asymmetric algorithms
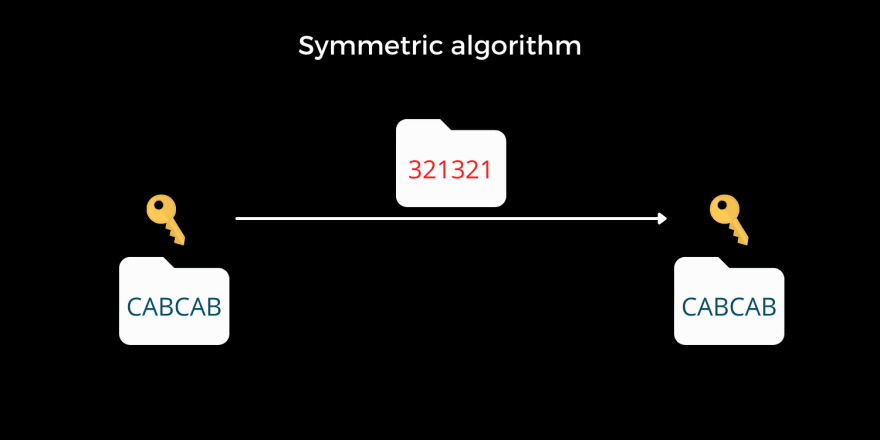
Symmetric algorithm
A symmetric algorithm uses the same key for both encryption and decryption. Remember, even though the middleman gets to know about the algorithm involved in the encryption process, the data is safe as long as they do not get access to the key. The previous substitution example ( CAB ) that we saw is a simple demonstration of symmetric algorithms. There is one issue here, the key must be protected even though both parties need it. Sending the key over the internet unencrypted is like announcing to everyone who hears it as to what the key is, to encrypt and decrypt the message.
Examples of symmetric algorithms: Advanced Encryption Standard ( AES ), ChaCha20, 3DES, Blowfish.
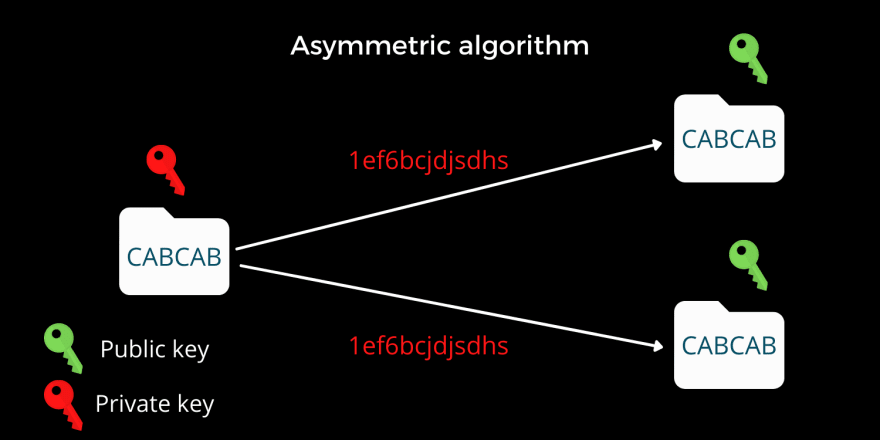
Asymmetric algorithm
Asymmetric algorithms use different keys for encryption and decryption. Here, you can encrypt the data using one key, and decrypt the data using another. Thanks to mathematics. Since computers are well known to handle computationally intensive mathematics, asymmetric algorithms became popular. Here, one can have two separate keys, where one of the keys can remain private and never needs to be shared with anyone.
The owner of the pair of keys will be sharing the public key with everyone and keeping the private key with him. There are two scenarios possible here with the pair of keys:
- Anyone with the public key will be able to encrypt the message with this public key and only the one who owns the private key ( the owner ) will be able to decrypt the message.
- The owner of the private key will encrypt a message with the private key, and anyone with the public key will be able to decrypt the message using the public key. Since the message can be only encrypted using the private key, and that is possible only by the owner, this technique ensures that it is indeed the owner who has encrypted the message, and this serves as a form of digital signature.
Examples of asymmetric algorithms: Diffie-hellman, RSA.
You can find more articles here: https://www.tharunshiv.com
Roadrunners is a series that is aimed at delivering concepts as precisely as possible. Here, a roadrunner is referred to as a person who does things super fast & efficiently. Are you a roadrunner?
Thank you
Original Link: https://dev.to/developertharun/encryption-decryption-for-r0drunner-12j3
Dev To
 An online community for sharing and discovering great ideas, having debates, and making friends
An online community for sharing and discovering great ideas, having debates, and making friendsMore About this Source Visit Dev To