An Interest In:
Web News this Week
- March 21, 2024
- March 20, 2024
- March 19, 2024
- March 18, 2024
- March 17, 2024
- March 16, 2024
- March 15, 2024
Top 10 Common Types of Cyber Security Attacks
1. Malware
Malware (short for malicious software) is a file or code, typically delivered over a network, that infects, explores, steals or conducts virtually any behavior an attacker wants. And because malware comes in so many variants, there are numerous methods to infect computer systems.
Types of Malware:
BotnetsShort for robot network, these are networks of infected computers under the control of single attacking parties using command-and-control servers.RansomwareIs a criminal business model that uses malicious software to hold valuable files, data or information for ransom.Spyware Malware that collects information about the usage of the infected computer and communicates it back to the attacker.TrojansMalware disguised in what appears to be legitimate software. Once activated, malware Trojans will conduct whatever action they have been programmed to carry out.VirusPrograms that copy themselves throughout a computer or network.WormSelf-replicating viruses that exploit security vulnerabilities to automatically spread themselves across computers and networks.
2. Phishing
Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information, or to install malware on the victims machine.
Types of Phishing:
Deceptive phishing- In this case, an attacker attempts to obtain confidential information from the victims. Attackers use the information to steal money or to launch other attacks.Spear phishing- Spear phishing targets specific individuals instead of a wide group of people. Attackers often research their victims on social media and other sites.Whaling- When attackers go after a big fish like a CEO, its called whaling. These attackers often spend considerable time profiling the target to find the opportune moment and means of stealing login credentials.Pharming- Similar to phishing, pharming sends users to a fraudulent website that appears to be legitimate. However, in this case, victims do not even have to click a malicious link to be taken to the bogus site
3. Man-in-the-Middle (MitM) Attacks
A man-in-the-middle (MitM) attack is when an attacker intercepts communications between two parties either to secretly eavesdrop or modify traffic traveling between the two. Attackers might use MitM attacks to steal login credentials or personal information, spy on the victim, or sabotage communications or corrupt data.
4. Denial-of-Service (DOS) Attack
A denial-of-service (DoS) attack is a security threat that occurs when an attacker makes it impossible for legitimate users to access computer systems, network, services or other information technology (IT) resources. Attackers in these types of attacks typically flood web servers, systems or networks with traffic that overwhelms the victim's resources and makes it difficult or impossible for anyone else to access them.
Types of DoS attacks:
Application layer- These attacks generate fake traffic to internet application servers, especially domain name system (DNS) servers or Hypertext Transfer Protocol (HTTP) servers.Buffer overflow- This type of attack is one that sends more traffic to a network resource than it was designed to handle.SYN flood- This attack abuses the TCP handshake protocol by which a client establishes a TCP connection with a server.Volumetric- These DoS attacks use all the bandwidth available to reach network resources. To do this, attackers must direct a high volume of network traffic at the victim's systems
5. SQL Injections
An SQL injection attack consists of an insertion or injection of a SQL query via the input data from the client to the application. SQL commands are injected into data-plane input that affect the execution of predefined SQL commands. A successful SQL injection exploit can read sensitive data from the database, modify database data (viz., insert, update, or delete), execute administrative operations on the database, recover the content of a file present in the database management system, and even issue commands to the operating system in some instances.
6. Zero-day Exploit
A zero-day vulnerability, at its core, is a flaw. It is an unknown exploit in the wild that exposes a vulnerability in software or hardware and can create complicated problems well before anyone realizes something is wrong. In fact, a zero-day exploit leaves NO opportunity for detection at first.
A zero-day attack happens once that flaw, or software/hardware vulnerability, is exploited and attackers release malware before a developer has an opportunity to create a patch to fix the vulnerabilityhence zero-day.
7. Password Attack
A password attack refers to any of the various methods used to maliciously authenticate into password-protected accounts. These attacks are typically facilitated through the use of software that expedites cracking or guessing passwords.
Types of Password Attacks:
Brute Force Attack- In a brute force attack, a hacker uses a computer program to login to a users account with all possible password combinations.Dictionary Attack- A dictionary attack allows hackers to employ a program that cycles through common words. A brute force attack goes letter by letter, whereas a dictionary attack only tries possibilities most likely to succeed.Rainbow Table Attack- A rainbow table attack is a type of hacking wherein the perpetrator tries to use a rainbow hash table to crack the passwords stored in a database system. A rainbow table is a hash function used in cryptography for storing important data such as passwords in a database.Credential Stuffing- Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a system.
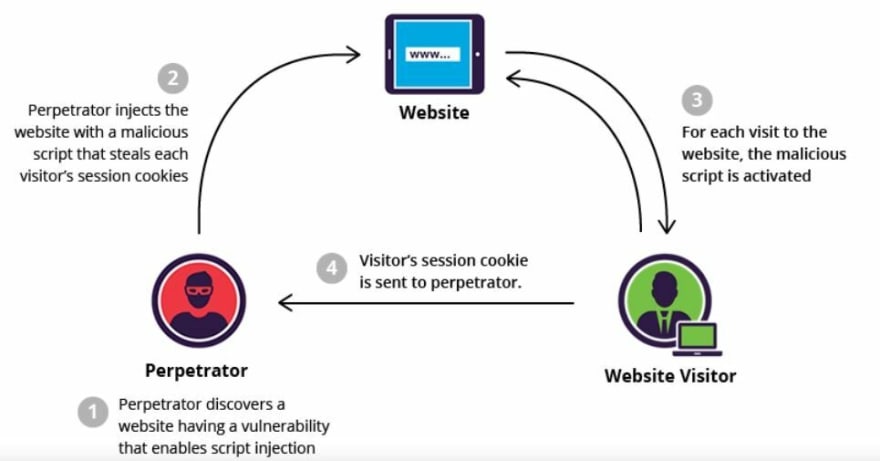
8. Cross-site Scripting
Cross-site Scripting (XSS) is a client-side code injection attack. The attacker aims to execute malicious scripts in a web browser of the victim by including malicious code in a legitimate web page or web application. The actual attack occurs when the victim visits the web page or web application that executes the malicious code. The web page or web application becomes a vehicle to deliver the malicious script to the users browser. Vulnerable vehicles that are commonly used for Cross-site Scripting attacks are forums, message boards, and web pages that allow comments.
9. Rootkits
A rootkit is software used by cybercriminals to gain control over a target computer or network. Rootkits can sometimes appear as a single piece of software but are often made up of a collection of tools that allow hackers administrator-level control over the target device.
Types of Rootkits:
Hardware or firmware rootkit- This type of malware could infect your computers hard drive or its system BIOS, the software that is installed on a small memory chip in your computers motherboard.Memory rootkit- This type of rootkit hides in your computers RAM, or Random Access Memory. These rootkits will carry out harmful activities in the background.Application rootkit- Application rootkits replace standard files in your computer with rootkit files. They might also change the way standard applications work. These rootkits might infect programs such as Word, Paint, or Notepad.Kernel mode rootkits- These rootkits target the core of your computers operating system. Cybercriminals can use these to change how your operating system functions. They just need to add their own code to it.
10. Internet of Things (IoT) Attacks
IoT attacks happen when bad actors try to compromise the security of an Internet of Things (IoT) device or network. When devices are compromised, attackers can steal or manipulate sensitive data, join IoT devices to a botnet, or take control of a system.
There are billions of IoT devices in the world, which all collect loads of data in real-time. These data, if intercepted, could supply an attacker with information about the environment in which the devices operate, about the users interaction with the devices, and even information about the user. Login credentials, health data, location data, and other sensitive personal data can be used for nefarious purposes by bad actors, and all of it could be obtained through IoT attacks.
Original Link: https://dev.to/darshangawade/top-10-common-types-of-cyber-security-attacks-3k52
Dev To
 An online community for sharing and discovering great ideas, having debates, and making friends
An online community for sharing and discovering great ideas, having debates, and making friendsMore About this Source Visit Dev To