An Interest In:
Web News this Week
- April 2, 2024
- April 1, 2024
- March 31, 2024
- March 30, 2024
- March 29, 2024
- March 28, 2024
- March 27, 2024
Protecting Your AWS Website From a DDoS Attack

An Update to Our Imperva Incapsula Series
This is the second of a sponsored, three-part series covering Incapsula performance and security services. In part one, I introduced you to Incapsula Website Security and walked through how easy it is to integrate your website with its systems—it literally takes only minutes and provides an incredibly broad set of sophisticated protections.
In this tutorial, I'll describe how Incapsula security can protect your Amazon Web Services-hosted website (as well as any website) from distributed denial of service attacks (DDoS).
Essentially, DDoS attacks are most often a coordinated attack from thousands of compromised "zombie" computers against a specific target—perhaps your website. It's not easy to defend against these attacks. Not only can DDoS attacks take down your services and ruin your customers' experience, but they can also lead to huge bandwidth overages and subsequent expenses.
In the next and third episode of this series, we'll move on to Incapsula CDN & Optimizer and other features such as compression and image optimization—most of this is available for free.
Incapsula is such an intriguing and sophisticated service that I hope to convince the editorial gods at Tuts+ to let me write more about it. If you have any requests for future episodes in this series or questions and comments on today's, please post them below. You can also reach me on Twitter @reifman or email me directly.
A Brief Recap of Incapsula

As I mentioned in part one, when you sign up for Incapsula, your website traffic will be seamlessly routed through its globally distributed network of powerful servers. Your inbound traffic is intelligently profiled in real time, blocking the latest web threats (e.g., SQL injection attacks, scrapers, malicious bots, comment spammers), and with higher-level plans, thwarting DDoS attacks. Meanwhile your outbound traffic is sped up with CDN & Optimizer. A lot of these features are provided for free, and you can try all of it without cost during their 14-day trials. If you have more questions already, check out the Incapsula FAQs.
Incapsula DDoS Protection
According to Imperva, "a recent industry study showed that some 75% of IT decision makers have suffered at least one DDoS in the past 12 months, and 31% reported service disruption as a result of these attacks."
Incapsula comprehensively protects your website from all three kinds of DDoS attacks:
- Volume based attacks
- Protocol attacks
- Application layer attacks
Incapsula comprehensively protects your website from all three kinds of DDoS attacks:
You can measure the financial liability of a DDoS attack on your company with the Incapsula DDoS Downtime Cost Calculator:

Here are sample results shown to me with my settings:

With the Incapsula Pro plan, you'll get a sophisticated Web Application Firewall (WAF) and backdoor protections to minimize liability and risk.
For protection against application layer DDoS attacks, you'll need the Business plan which begins at $299 per site per month. The Enterprise plan offers protection from network layer attacks.

Incapsula DDoS protections will work whether you host your website at AWS or any web host. Here's how they are delivered and what they provide:
- Provided as a powerful network of globally positioned Data Centers
- Application (Layer 7) and Network (Layers 3,4) DDoS protection
- Backed by a 24x7 security team and a 99.999% uptime SLA
- Available as an always-on or on-demand service
Here's a map of the Incapsula network's global data centers:

You can see how your actual visitors and DDoS traffic are managed by Incapsula before they reach your website (often mirrored by Incapsula for performance):

There's also blanket DDoS protection for all types of services (UDP/TCP, SMTP, FTP, SSH, VoIP, etc.) when you sign up for infrastructure protection for an individual IP address.
Individual IP protection enables users to deploy DDoS Protection to defend all types of environments, including:
- Cloud environments (e.g., AWS, Azure)
- Gaming servers (and other devices using proprietary protocols)
- Individual networked devices and origin servers
When you join this service, Incapsula will assign you an IP address from our own IP range for routing traffic. A tunnel is then established between your origin servers (or routers/load balancers) and the Incapsula network. Once in place, this tunnel is used to route clean traffic from our network to your origin, and vice versa. You then broadcast the assigned IP addresses to your users via DNS, making these your nominal “origin” addresses.

Before we explain more about Incapsula advantages for AWS customers, let's walk through more about DDoS attacks and networking terminology.
How DDoS Attacks Operate
The image below (from Wikipedia) shows how an attacker leverages an untraceable network of computers and compromised "zombies" to bring a web application to its knees:
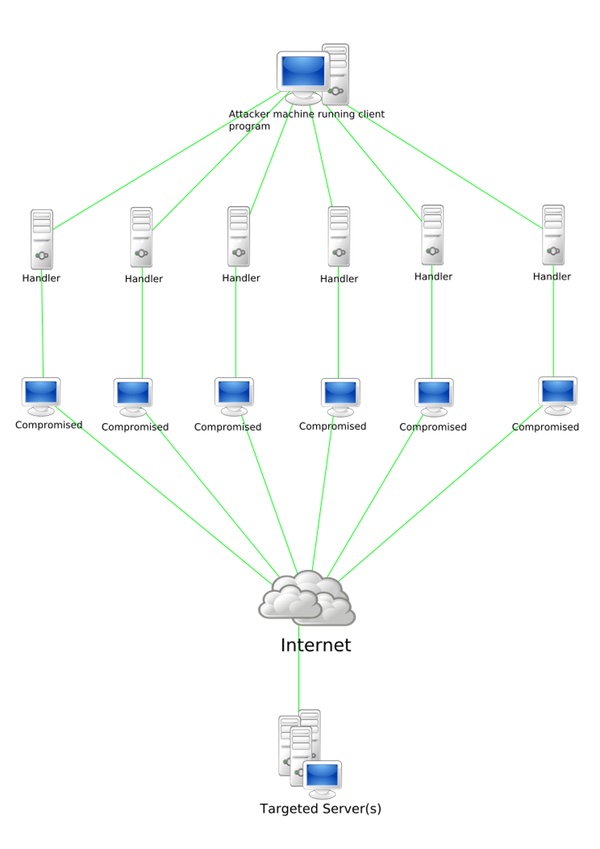
Incapsula DDoS protections work at the Application (Layer 7) and Network (Layers 3 and 4) of the Seven Layers of the OSI Model. Here's Wikipedia's guide to these layers for more detail:

While it may seem complex, these are essentially the layers that DDoS attacks use, as those are the ones that connect your website to Internet users and other computers on the Internet.
The Incapsula Five-Ring Approach to DDoS Protection
From a conceptual standpoint, Incapsula DDoS protection is based on a set of concentric rings around the application, each of which filters a different portion of the traffic. Each of these rings by itself can be easily bypassed; however, working in unison they stop almost all malicious traffic. While some DDoS attacks may be stopped at the outer rings, persistent multi-vector attacks can only be stopped by using all (or most) of them.

As such, Incapsula defends against all kinds of hacking attempts and attacks including Open Web Application Security Project (OWASP) top ten defined threats:
- Injection
- Broken Authentication and Session Management
- Cross-Site Scripting (XSS)
- Insecure Direct Object References
- Security Misconfiguration
- Sensitive Data Exposure
- Missing Function Level Access Control
- Cross-Site Request Forgery (CSRF)
- Using Components with Known Vulnerabilities
- Unvalidated Redirects and Forwards
Here's how the Incapsula solution five-ring approach operates:
Ring 5: Client Classification vs. Volumetric Layer 7 Attacks. In some cases, attackers may use a volumetric application layer attack (e.g. HTTP flood) as a distraction intended to mask other more targeted attacks. Incapsula uses client classification to identify and filter out these bots by comparing signatures and examining various attributes: IP and ASN info, HTTP headers, cookie support variations, JavaScript footprint, and other telltale signs. Incapsula distinguishes between humans and bot traffic, between "good" and "bad" bots, and identifies AJAX and APIs.
Ring 4: Visitor Whitelisting and Reputation. After flagging and blocking the malicious volumetric traffic, Incapsula partitions the rest of the website traffic into "grey" (suspicious) and "white" (legitimate) visitors. This task is supported by the Incapsula reputation system.
Ring 3: Web Application Firewall for Direct Attack Vectors. In addition to offering DDoS protection, the Incapsula solution includes an enterprise-grade Web Application Firewall (WAF) that protects websites from any application layer threat, such as SQL injection, cross site scripting, illegal resource access and remote file inclusion. WAF utilizes sophisticated traffic inspection technology and crowdsourcing techniques, coupled with extensive expertise delivering end-to-end application security. Advanced features include a custom rules engine (IncapRules, reviewed below), backdoor shell protection, and integrated two-factor authentication (reviewed in part one.)
Ring 2: Progressive Challenges. Incapsula applies a set of progressive challenges that are designed to ensure the optimal balance between strong DDoS protection and an uninterrupted user experience. The idea is to minimize false positives by using a set of transparent challenges (e.g. cookie support, JavaScript execution, etc.) to provide pinpoint identification of the client (human or bot, "good" or "bad").
Ring 1: Behavioral Anomaly Detection. Incapsula uses Anomaly Detection rules to detect possible instances of sophisticated Layer 7 attacks. This ring acts as an automated safety net to catch attacks that may have slipped through the cracks.
Ring 0: Dedicated Security Team. Ultimately, your experience with Incapsula is supported by Imperva's team of experienced Security Operations Center professionals and 24x7 support staff. They proactively analyze the internal behavior of the application and detect irregular usage before any problem becomes widespread.
Below, Incapsula mitigates a 250GBps DDoS attack—one of the Internet's largest:

Furthermore, the Incapsula Web Application Firewall is PCI-certified (PCI was created by global credit organizations such as American Express, MasterCard, and Visa):
The PCI Security Standards Council is an open global forum, launched in 2006, that is responsible for the development, management, education, and awareness of the PCI Security Standards, including the Data Security Standard (PCI DSS), Payment Application Data Security Standard (PA-DSS), and PIN Transaction Security (PTS) requirements.
Of course, DDoS Protection is implemented outside your network. This means that only filtered traffic reaches your hosts—protecting your investment in hardware, software, and network infrastructure, while simultaneously ensuring the continuity of your business.
Incapsula DDoS Protection for AWS
Whether you host your application with AWS or not doesn't actually matter, because the DDoS protective capabilities of the Incapsula solution will safeguard your website. But, if you are an AWS customer, do not be fooled into thinking Amazon will fully protect you—Incapsula provides significant additional protections.
Like most hosting platforms, AWS is not a security platform. While it offers basic DDoS mitigation capabilities, such as SYN cookies and connection limiting, it's not built to defend hosted servers and applications. If your web server gets hit by an application (layer 7) DDoS attack, AWS will not protect you. Worse yet, if you suffer a massive network (layers 3 and 4) DDoS attack, you will be charged for the additional bandwidth and receive a huge bill at the end of the month. Anyone who's dealt with Amazon customer service knows getting refunds isn't always easy.
Incapsula complements AWS with its cloud-based DDoS protection service. This service enhances AWS’s basic security capabilities so that your critical applications are fully protected against all types of DDoS attacks.
Using advanced traffic inspection technology, Incapsula DDoS Protection for AWS automatically detects and mitigates volumetric network (OSI layer 3) and sophisticated application (layer 7) DDoS attacks—with zero business disruption to users.
Its always-on service secures AWS-based websites and applications against all types of DDoS attacks—from massive volumetric network (OSI layers 3 and 4) barrages to sophisticated application (layer 7) assaults. Automatic detection and transparent mitigation of DDoS penetrations minimizes false positives, ensuring a normal user experience—even when under attack.
Want to Experiment With Incapsula and AWS?
If you'd like to experiment with Incapsula and AWS with a sample EC2 instance and simple guide, follow my Tuts+ installation guide for WordPress in the Amazon Cloud and then use part one of this series to sign up for Incapsula and make the simple DNS changes to integrate it with your website. As I describe in that episode, the results take hold quickly and impressively.
Of course, if you're using Amazon's DNS service Route53, it's just as easy to configure your site as I described in part one with my generic DNS service.
Simply log in to the Route53 management console and then browse to your domain record sets. From the list of records, select the subdomain you are adding to Incapsula and edit the record in the Edit Record Set dialog.
If you're using a CNAME, it looks like this:

If you're using a www. or naked domain and an A record, it looks like this:

If you prefer just a visual walkthrough, check out the Incapsula demonstration site and some of these excellent resources about Incapsula DDoS protections for AWS.
Firstly, there's the Incapsula DDoS Protection Overview (pdf) (screenshot below):

There are also these helpful, detailed references:
- DDoS Response Playbook (ebook)
- How to Prepare Your DDoS Protection Strategy (whitepaper)
- Preparing for the Terabit Scale DDoS Attack (webinar)
And, there's also a DDoS landing page for generic hosts (non-AWS).
Incapsula servers perform robust, deep packet inspection to identify and block malicious packets based on the most granular of details. This permits them to instantly examine all attributes of each incoming packet, while simultaneously serving hundreds of gigabits of traffic at an inline rate.
The 700+ Gbps Incapsula network of global scrubbing centers mitigates the largest DDoS attacks—including SYN flood and DNS amplifications, which can exceed 100 Gbps. The Incapsula network scales on demand to counter massive volumetric DDoS attacks. This ensures that mitigation is applied outside your own network, allowing only filtered traffic to reach your hosts.
Soon, Incapsula will provide the individual IP infrastructure protection I mentioned above for AWS customers. Once configured, you can use Amazon's security groups to ensure all external traffic is restricted to originate from inside Incapsula. This eliminates outside attackers from ignoring your services with Incapsula and attacking you directly. Essentially, you just configure security groups to restrict by Incapsula network IP addresses.
And yes, you can still use your CloudFront domain for serving static files while using Incapsula for DDoS mitigation and AWS's Route 53 DNS.
Managing Your Site Security With Incapsula
I reviewed the initial elements of this in episode one; once your site is configured, you'll see it listed on the dashboard:

The Incapsula Settings provide you complete control over its wide variety of powerful features. You can see the DDoS configurations from the Web Application Firewall (WAF) sub-menu:

From there, you can configure the behavior of your DDoS. Under Advanced Settings you can instruct Incapsula on when and how to challenge suspected attackers:

You can also whitelist IP addresses, URLs, certain countries and more:

IncapRules Filter Events and Trigger Actions
The dashboard's Events area helps you filter, identify and begin responding to attacks of all sorts, including DDoS:

With help from here or from your own specifications, you can configure rules to filter, alert you and respond automatically to these kinds of attacks. They are called IncapRules. The IncapRules sub-menu provides complete descriptions about how to define more detailed rules.

Adding and managing the List of Rules is quite easy:

IncapRules allow you to take advantage of the Incapsula network's entire range of powerful traffic inspection abilities. With them you can create custom policies based on HTTP header content, geolocation, and much more.
IncapRules syntax relies on descriptively-named ‘Filters’ and a set of logic operators. Combined these are used to form a security rule (a.k.a. ‘Trigger’) that leads to one of the pre-defined ‘Actions’. Here are a few examples:
In this image, we're configuring a rule to require cookies if more than 50 sessions are active while allowing higher activity from specific IP addresses or Google Search bots.

To counter brute force attacks, you can deploy a relatively simple rule, to limit the number of subsequent POST requests to your login page. For example, this simple Filter will be triggered by more than 50 subsequent POST requests made by inhuman (non-browser) visitors within the span of a minute:
Rate > {post-ip;50} & ClientType != Browser [Block Session]Once triggered, such rule can respond with any number of actions. In this case, the rule is set to [Block Session] that will instantly terminate the session. Alternately, you can set the action to [Alert], which will transparently notify you about the incident with email and GUI messages.
Of course, generic rate thresholds can disrupt the user experience improperly. For example, you might want to restrict this to your API and higher-than-normal request rates. One thing you can do is to tweak the rule syntax with the [URL] filter, to create a rule that won’t be triggered by POST requests to API URLs:
Rate > {post-ip;50} & URL != /api & ClientType != Browser [Block IP]When employing multiple filters with various logical operators (e.g. and/or, larger/smaller than, and, etc.) to link between them, the IncapRules filter set offers limitless combinations—letting you create custom security policy for every type of scenario.
You can learn more about IncapRules and protection against brute force attacks here, or feel free to give it a try!

What Will We Explore Next?
I hope you're enjoying learning about Incapsula DDoS Protection. When I gave the Incapsula solution a try, I was thoroughly impressed with the simple integration and broad array of powerful protective capabilities. If your website application might be susceptible to large-scale attacks, its DDoS protections will prove incredibly valuable and cost-efficient.
Next up, I'll delve deeply into Incapsula CDN & Optimizer, starting with the free plan, which includes a content delivery network, minimization, image compression, TCP Optimization, Connection Pre-Pooling and many more features.
Please feel free to post your questions and comments below. You can also reach me on Twitter @reifman or email me directly. You can also browse my Tuts+ instructor page to read the other tutorials I've written.
Related Links
- Overview of Incapsula DDoS Protection
Incapsula DDoS Protection for Amazon Web Services (AWS)
Incapsula Five-Ring Approach to Application Layer DDoS Protection
Download Incapsula DDoS Protection Overview (pdf)- DDoS Response Playbook (ebook)
- How to Prepare Your DDoS Protection Strategy (whitepaper)
Preparing for the Terabit Scale DDoS Attack (webinar)
How to Secure Your Website With Imperva Incapsula (Tuts+)
Incapsula Frequently Asked Questions- Incapsula Video Channel
Original Link:
TutsPlus - Code
 Tuts+ is a site aimed at web developers and designers offering tutorials and articles on technologies, skills and techniques to improve how you design and build websites.
Tuts+ is a site aimed at web developers and designers offering tutorials and articles on technologies, skills and techniques to improve how you design and build websites.More About this Source Visit TutsPlus - Code

